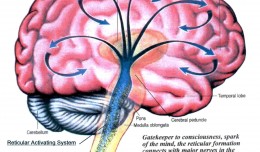
Tweaking your Critical Factor … Understanding RAS
In previous posts (probably over a year ago now) I have spoken about this thing called the critical factor. In the hypnosis world this is the gatekeeper or firewall between your conscious and subconscious mind, helping to kee...