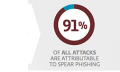
Why Social Engineering Works … Infograph by Veracode
I came across this great infograph from Veracode today on “Why Social Engineering Works”. Wish I had the time and the skill to put these infographs together, but here you go. (Its a relatively large file so please b...
Joe Navarro’s Body Language Academy
Last year I signed up to do the Body Language Expert training course with Joe Navarro’s Body Language Academy. The training is self paced and expected to take you around 4 – 6 months, however once I got going and du...
Parvum S1.0 … Cracking Passwords In Style
Marty McFly: Wait a minute, Doc. Ah… Are you telling me that you built a time machine… out of a DeLorean? Dr. Emmett Brown: The way I see it, if you’re gonna build a time machine into a car, why not do it with...
This or That … The Fatal Aggressive Close
Influence and or manipulation is always an interesting topic, and we may often ask ourselves why we came to the conclusion that made us act in a certain way. In the past I have spoken about how we can do the mini brain buffer o...
Just Called To Say … Spoofed Your Caller ID
The aim of this post is to share tools for Social Engineers to include vishing in you engagements, and to make the rest of the world aware of just how simple and easy it is to Spoof someones Caller ID, so you can increase your ...